Chinese Certificate Authority 'mistakenly' gave out SSL Certs for GitHub Domains
A Chinese certificate authority (CA) appeared to be making a significant
security blunder by handing out duplicate SSL certificates for a base
domain if someone just has control over its any subdomain. ..
The certificate authority, named WoSign, issued a base certificate for the Github domains to an unnamed GitHub user.
But How? First of all, do you know, the traditional Digital Certificate Management System is the weakest link on the Internet today and has already been broken?
Billions of Internet users blindly rely on hundreds of Certificate Authorities (CA) around the globe to ensure the confidentiality and integrity of their personal data.
The certificate authority, named WoSign, issued a base certificate for the Github domains to an unnamed GitHub user.
But How? First of all, do you know, the traditional Digital Certificate Management System is the weakest link on the Internet today and has already been broken?
Billions of Internet users blindly rely on hundreds of Certificate Authorities (CA) around the globe to ensure the confidentiality and integrity of their personal data.
But, these CAs have powers to issue valid SSL cert for any domain you own, despite the fact you already have one purchased from another CA.
...and that's the biggest loophole in the CA system.
In the latest case as well, WoSign issued a duplicate SSL certificate for GitHub domains without verifying ownership of the base domain.
The incident was first publicly disclosed by British Mozilla programmer Gervase Markham on Mozilla's security policy mailing list saying the issue occurred over a year ago in July 2015 but went unreported.
"In June 2015, an applicant found a problem with WoSign's free certificate service, which allowed them to get a certificate for the base domain if they were able to prove control of a subdomain," Markham wrote in the mailing list.According to Markham, an unnamed security researcher accidentally discovered this security blunder when trying to get a certificate for 'med.ucf.edu' but mistakenly also applied for 'www.ucf.edu' and WoSign approved it, handing over the certificate for the university's primary domain.
For testing purpose, the researcher also used this trick against Github base domains i.e. github.com and github.io, by proving his control over a user-based subdomain.
...And guess what? WoSign handed over the certificate for GitHub main domains, too.
The researcher reported this issue to WoSign by giving only the Github certificate as an example. Thus, the Chinese CA only revoked the GitHub certificate, despite revoking both the certificates.
Why Just One? It is quite possible that the CA company doesn't have any tracking ability to discover and revoke all mistakenly issued base certificates for other domains by self-investigation even after getting informed of the problem.
The researcher recently got in touch with Google and reported that the ucf.edu cert had still not been revoked almost a year later.
How to check whether a rogue cert for your domain has been issued to someone else, probably a malicious attacker?
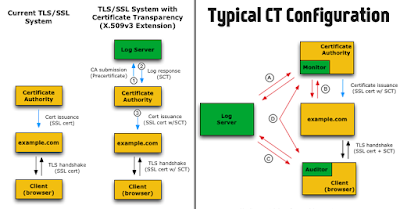
Solution: Certificate Transparency or CT, a public service that allows individuals and companies to monitor how many digital security certs have secretly been issued for their domains.
Certificate Transparency requires CAs to declare publicly (to Certificate Log) every digital cert they have generated. Even WoSign has participated in CT.
Certificate Log offers you a way to look up all of the digital certificates that have been issued for your domain name.
Also read: Learn How Certificate Transparency Monitoring Tool Helped Facebook Early Detect Duplicate SSL Certs?
Although Certificate Transparency doesn't prevent CA from issuing forged certificates, it makes the process of detecting rogue certificates much easier.
Currently, Google, Symantec, DigiCert, and a few other CAs are hosting public CT logs.
You can try Google's Certificate Transparency Lookup Tool or Comodo's Certificate Transparency Search tool to check all certificates present in public Certificate Transparency logs that have been issued for your domain.
If you find a fraud certificate issued for your domain, report respective CA and address it immediately.





Post a Comment